Last night, Twitter user and well known NFT personality @NFT_GOD (~90k followers at time of writing) announced that he was hacked. As a result of the hack, he claimed to have lost all his digital assets and had his accounts compromised.
Potentially even worse than having his assets stolen, compromised emails were sent to his approximately 16.000 newsletter subscribers, further endangering his closest community. At the current time, it is not clear whether anyone else has lost any funds due to the scam emails. In this article, we will look at what happened, how his assets were stolen despite owning a cold wallet, which is supposed to protect you from most attacks, and what you can learn from this hack to protect yourself.
As you will see, several unlucky circumstances had to coincide for him to lose his valuable NFTs. This can basically happen to everyone so this article is to share the potential risk and protect other users.
Summary
- NFT God accidentally clicked on a Google ad that forwarded him to a malicious website and
- downloaded malware onto his PC, which didn’t get picked up by his antivirus (if he had one).
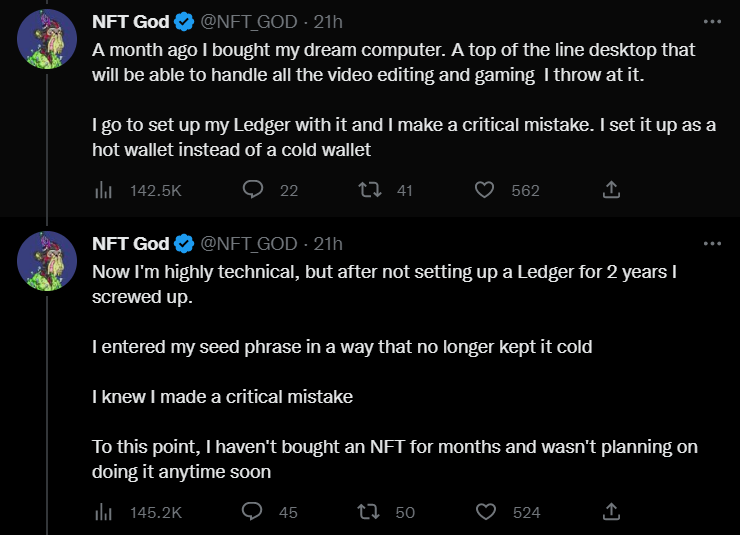
- Due to an inadvertent connection of his cold wallet and MetaMask, the hackers were able to steal his seemingly secured assets.
The main mistake: when MetaMask asked whether he would like to create a new account or import an existing one it looks like he imported his Ledger seed phrase instead of his MetaMask seed phrase. That is effectively turning a cold wallet (not connected to the internet) into a hot wallet (always connected). If you want to read more about this, click here.
What led to the hack and which habits help you to avoid it?
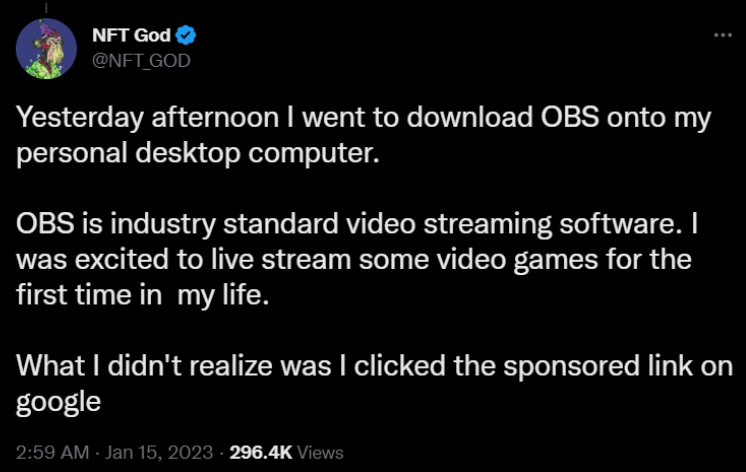
According to NFT God, the mutant ape holder recently purchased his dream computer. However, unbeknown to him, his purchase would quickly turn into a nightmare.
While happily working away at downloading and installing all of his favorite software, NFT God turned to everyones’ preferred search engine, Google, to find the official download for OBS, an open-source video capture and streaming program popular with content creators and streamers alike. Unfortunately, this is where the trouble began. Instead of clicking on the official OBS website in the search results (which is the first non-ad result), NFT God clicked on the first search result altogether, which is often an ad.
See the following screenshot for an example of Google paid adverts vs. organic search results:
Habit #1: Don’t follow Google ads if you want to download software
“Isn’t Google a legit company?” you might ask yourself? Sure – you are right, but there are unfortunately several issues with paid advertisements in Google search.
Most importantly: Google fights and bans an enormous amount of scam advertising accounts every day. However: Bad actors still abuse the Google Search Engine Advertisement (short “SEA”) to get fake websites to the top of the results. They create identical copies of popular websites and use similar looking domains to trick the user into thinking that they are using the official site. Tools that offer free downloads get targeted the most.
How can you protect yourself? Carefully consider before clicking on search results that are denoted with “Ad”, as seen in the screenshot above. Especially when you want to download software.
Furthermore, avoid downloads from third-party websites. It is good practice to only get your downloads from trustworthy official websites of the tool/company that creates the program. This is how you will get the most up-to-date version of the software. Otherwise you might end up downloading malware without knowing it.
After clicking onto the fake website, the NFT celebrity clicked on the download button and went to install OBS as usual. He clicked the .exe installer, but nothing happened. Or did it?
Habit #2: Run a good antivirus program!
While we can only speculate at this point: it is likely that he either disabled the built-in windows defender. Or he got very unlucky and encountered a fresh “RAT” (remote access trojan), which was not detectable yet. While Windows Defender, the built-in antivirus found on all modern Windows installs, has greatly improved over time, it is still somewhat lacking in some departments, especially the real-time scanning of downloaded files (See: https://cybernews.com/best-antivirus-software/microsoft-defender-review).
While this should not be an issue if you only download your programs from trusted sources, you might prefer to be “rather safe than sorry”.
That’s why it can be a good idea to utilize a (paid) antivirus program. Some favorites from our office include ESET Internet Security and Norton, which both score very high in antivirus tests by AV-TEST (https://www.av-test.org/en/antivirus/home-windows/manufacturer/eset/ and https://www.av-test.org/en/antivirus/home-windows/manufacturer/norton/ respectively).
“But I use a Mac, so I don’t need an antivirus, right?”
Wrong. Unfortunately, nowadays Macs also get targeted by a lot of malware, especially adware. On average, Macs get targeted twice as much as a windows PC, even if the severity of the exploits is usually less. (https://www.tomsguide.com/news/mac-malware-rate-report).
Bonus tip for Windows Defender Users: How to harden your system
If you don’t mind going through a bit of extra work while setting up your system, and you don’t very frequently add new software to your install, turning on controlled folder access in Windows Defender will give your security a big boost. With this feature enabled, you will have to explicitly grand every tool the rights to modify only specific folders on your system. This also means that you will be able to see when that new streaming software you just installed suddenly tries to access all of your documents and system files.
This feature can be found under Settings → Privacy and Security → Windows security → Virus & threat protection → Ransomware protection → Controlled folder access.
Alright, so NFT God somehow got a trojan onto his newly installed desktop. But surely, someone who owns a Mutant Ape Yacht Club NFT (minimum approximate value at time of writing: ~US$25,000) as well as plenty of other digital assets uses a cold wallet to ensure no one is able to steal them? Yes. Kind of.
Habit #3: Never import your cold wallet seed phrase into MetaMask
Of course, like all diligent crypto users, NFT God owns a hardware wallet. Hardware wallets (like the Ledger and Trezor products) ensure that your assets are kept safely in offline storage whenever they are not connected to the internet (this is also called “cold storage”) so your account can’t easily be drained of funds should a hacker gain access to your PC. But the crypto influencer made one critical mistake:
When you first install the MetaMask extension, you will encounter this screen:
Due to the way MetaMask words this page, it is very easy to think “No, I’m not new to MetaMask, and I already have a wallet I want to keep using! My Ledger!”
So you click on “Import wallet” and enter the seed phrase you received when you first set up your Ledger. Just like that, your cold wallet has been imported into MetaMask and is now a “hot wallet”, connected to the internet like any normal MetaMask.
What went wrong?
When you import a Ledger’s seed phrase into MetaMask, the wallet app will use the seed phrase to re-generate your private keys and store them inside the application. This is a handy feature in case you ever lose your Ledger. However, if you plan on continuing to use your Ledger as a cold wallet, youshould never enter your Ledger seed phrase anywhere but in the Ledger itself (and that only needs to be done in case you have to recover your account).
When migrating a MetaMask to a new PC, only use the MetaMask seed phrase to transfer the account.
What if I made the same mistake? Do I have to purchase a new Ledger?
The short answer here is: No.
The hardware of your Ledger is still in working order. Unless you already have malware on your computer, you are most likely fine for the short term.
Before you follow these steps, ensure that you are able to send funds from your wrongly imported MetaMask wallet to any other wallet without having to confirm the transaction on the Ledger.
It also doesn’t hurt to keep the Ledger seed phrase that you used to import the wallet during the MetaMask setup.
To restore the protective properties of your hardware wallet, follow these steps:
- Reset your Ledger (see: https://support.ledger.com/hc/en-us/articles/360017582434-Reset-to-factory-settings- for detailed instructions) to create a new private key and seed phrase.
- Use the Ledger app to create a new wallet
- Transfer your funds and assets from the MetaMask account to your newly created Ledger wallet.
Yes, you will have to pay gas fees for the different transfers. But that’s still way better than losing your assets.
How to correctly use your hardware wallet with MetaMask
The only way to safely utilize your hardware wallet together with MetaMask to sign transactions is by using MetaMask’s own “Connect hardware wallet” feature.
Currently, MetaMask supports four different kinds of hardware wallets:
More information on using hardware wallets can be found on MetaMask’s official support website: https://metamask.zendesk.com/hc/en-us/articles/4408552261275-Hardware-Wallet-Hub
Final words
The loss of your hard-earned assets is devastating.
None of the mistakes in themselves were particularly “dumb” or obvious. We’ve all been there – we are excited about setting up a new device, maybe we missed one or two hours of sleep, and we become a bit careless. It is easy to point fingers and say “well, that’s just user error” (something particularly popular in the crypto and the Linux communities). But the truth is: bad user-interfacing and wording played a significant role in the loss of these assets too.
If MetaMask very explicitly warned you against importing hardware wallet seed phrases during the setup, users would be a lot less likely to make such a mistake. In order to make Crypto and Web3 more accessible to the masses, user interfaces have to be improved and the likelihood of making grave mistakes has to be decreased.
Let these bad news be a warning: the internet isn’t a safe place. Bad actors will always try to separate you from your precious assets. That’s why it is especially important that you stay vigilant and follow the best practices outlined above.
Finally, this hack doesn’t prove that hardware wallets are a bad way of securing your assets – they are actually one of the best. But guard your seed phrase closely, and be very careful where you input it.